ESET Research last Friday released its analysis of Asylum Ambuscade, a cybercrime group that has been performing cyberespionage operations on the side. The group has been running cyberespionage campaigns since at least 2020. ESET found previous compromises of government officials and employees of state-owned companies in Central Asian countries and Armenia. In 2022 the group reportedly targeted government officials in several European countries bordering Ukraine. ESET Research assesses that the goal of the attackers was to steal confidential information and webmail credentials from official government webmail portals. Asylum Ambuscade usually targets small- and medium-sized businesses (SMBs) and individuals in North America and Europe.
In 2022, when the group targeted government officials in several European countries bordering Ukraine, the compromise chain started with a spearphishing email containing a malicious Excel spreadsheet or Word document attachment. If the machine was deemed interesting, the attackers eventually deployed AHKBOT, a downloader that can be extended with plugins to spy on the victim’s machine. These plugins provide various capabilities, including taking screenshots, recording keystrokes, stealing passwords from web browsers, downloading files and executing an infostealer.
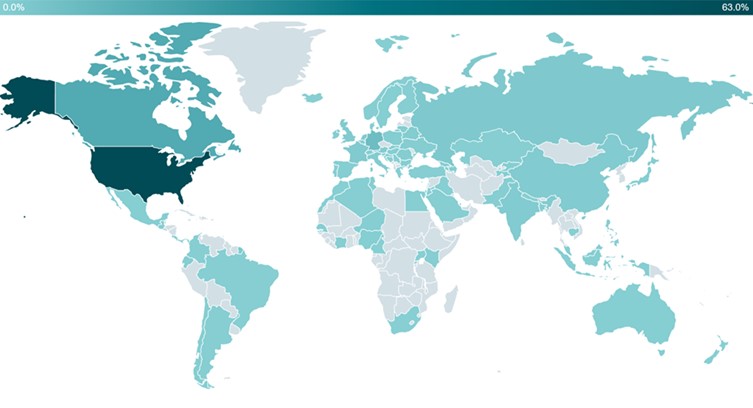
Even though the group entered the spotlight because of its cyberespionage operations, it has mostly run cybercrime campaigns since early 2020. Since January 2022, ESET Research has counted more than 4,500 victims worldwide. While most of these are located in North America, it should be noted that we have also seen victims in Asia, Africa, Europe and South America. Targeting is very wide and mainly includes individuals, cryptocurrency traders, bank customers, and SMBs in various verticals.
ESET Researcher Matthieu Faou (who investigated the activities of the group)
It appears Asylum Ambuscade is branching out, running some recent cyberespionage campaigns on the side, against governments in Central Asia and Europe from time to time. It is quite unusual to catch a cybercrime group running dedicated cyberespionage operations, and as such we believe that researchers should keep close track of its activities... Asylum Ambuscade’s crimeware compromise chain is, overall, very similar to the one we see for their cyberespionage campaigns. The main difference is the compromise vector, which could be a malicious Google Ad redirecting to a website delivering a malicious JavaScript file or multiple HTTP redirections.