5G is likely to be one of the most significant technological and societal disruptors of the decade. It is not just about being faster, bigger, or better, it’s about utilizing 5G as an enabler to a series of services that we all will consume in every aspect of our lives. While previous generation of mobile technologies like 2G & 3G were designed to connect people through voice & text, and 4G was designed to connect people through internet, 5G is about connecting people to services, the internet, and things. Use-cases like autonomous cars, integrated smart cities, augmented & virtual reality, interconnected social networks and devices will be ubiquitous.
However, as the number of 5G deployments grows around the world, the time has come to think of security considerations for 5G deployments. While 3GPP has standardised 5G to be the most secure mobile technology, it differs from previous generations of mobile technologies in that it requires networks to be re-architected for software defined networking (SDN), Network Function Virtualization (NFV) and cloud native architecture for scalability. The convergence of 5G and IoT adds to the existing threat surface that requires careful consideration from a cyber risk perspective. The time has come to consider the security implications and cyber risk associated with 5G, whether it is business risk, financial risk, or regulatory risk, and this applies not only to companies that provide 5G services but to the ones that consume it as well.
3GPP Security enhancements for 5G in Release 15 & 16
5G is the first mobile technology designed for the cloud, leveraging cloud security best practices to protect networks, applications, and data while also introducing new cloud security risks. In releases 15 and 16, 3GPP standardised and improved security standards. The importance of data confidentiality and integrity, as well as authentication and authorisation of both user devices and network infrastructure, is emphasised. The various security considerations for 5G network security falls both on end user devices and the network infrastructure. Some important aspects to consider are
- Network authentication and end user equipment authorization
- Encryption of user data in transit and signaling
- Secure services-based architecture
- Network slice specific authentication and authorization
- Use case specific security enhancements for cellular IoT and URLLC services.
- API Security
Each generation of mobile technology is more secure that its predecessor. Nevertheless, our risk tolerance has decreased due to increased impact a cyberattack on a 5G network as we increasingly rely upon it for critical infrastructure and mission critical applications.
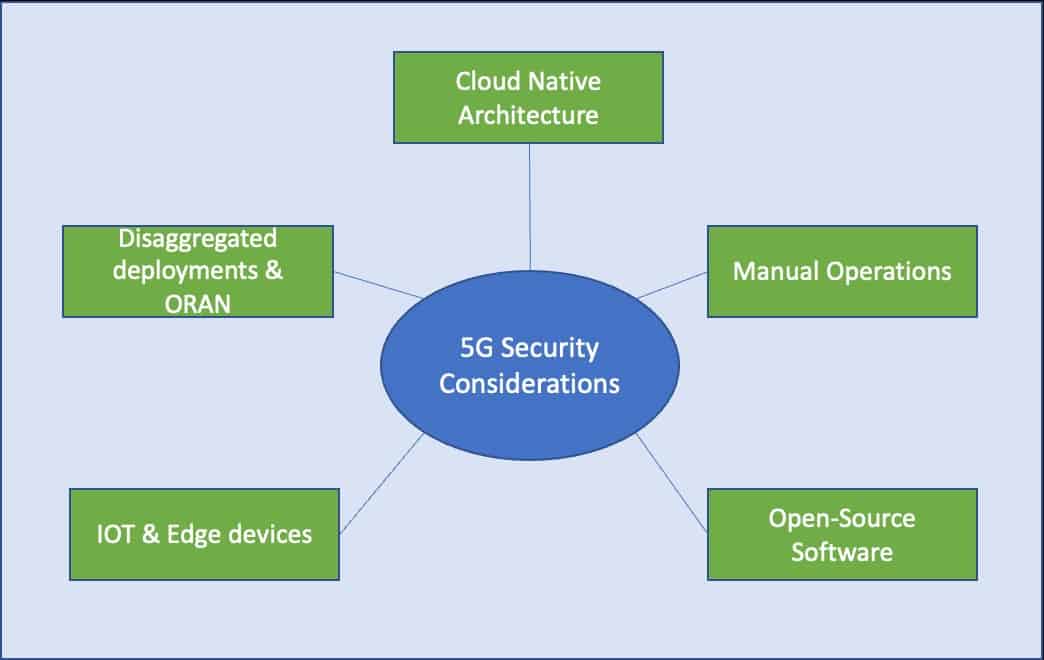 Fig 1: 5G Security considerations
Fig 1: 5G Security considerations
Key considerations for 5G network security
Let’s look at the key drivers that lead to redesign of 5G security architecture.
- Cloud Native Architecture: The 5G takes advantage of cloud native architecture where network functions are virtualised as VNF/CNF. These network elements communicate with each other to deliver services and applications. The cloud-native architecture allows for a scalable, automated environment where network, compute and storage services can expand, and contract as needed. Many telecommunications and mobility functions can now be hosted as software services and dynamically instantiated in different network segments. However, the cloud native architecture introduces some security vulnerabilities like penetration attacks, resource theft, and Man-in-the-middle attack. Virtualization technologies may pose a Denial of Service (DoS) risk. Some of the exposed API may make it easier to exploit loopholes and get unauthorised access.
- Disaggregated Deployments & ORAN: The initial 5G deployment are mostly non-stand-along (NSA) which does not significantly change the security risk too much from previous 4G deployments. However, with 5G Stand-alone (SA) the security landscape changes fundamentally.In a 5G SA, an attacker can launch a downgrade attack to 4G then leverage security vulnerabilities of 4G. Aside from core networks, the 5G New Radio (NR) is the global standard for open, interoperable, and disaggregated networks. While ORAN has advantages in terms of agility and efficiency, it introduces new security risks as more functions, interfaces, and open-source code is added.
- IOT & Edge Devices: 5G serve not only individual mobile users but also enterprises, industries, and the broader society. With the new services that 5G brings, operators will require a flexible security mechanism for each type of service. In Edge deployment many of the operators many operators have virtualised components. Edge devices may have to be physically secured along with the underlying software platform. The number of edge devices are also significantly more, and these devices may come from variety of vendors. Not all these devices may have necessarily gone through the required security testing and certification.
- Open-Source Software: Although open-source software has many benefits in terms of shortened time to market and total cost, it also has vulnerabilities that put application security at risk. Because the code is readily available, attackers can easily spot flaws and introduce harmful code. The code may not always be adequately tested and patched for known vulnerabilities with the most recent release.
- Manual Operations: Traditionally network management had network engineers manually logging into infrastructure to configure or trouble shoot. Manual operations are no longer sufficient with 5G and the fact that the threat landscape continues to grow in volume and sophistication. Security must be fully automated, including threat detection and mitigation.
Recommendations for 5G network security
As we have seen 5G networks faces new security threads due to its unique architecture and services. Now let’s look at some of the mitigating actions that can be considered. This is by no means a comprehensive list but some of the aspects to be considered
- Cloud Native security: Ensure that security is embedded in entire lifecycle management from development to production. The key security controls and processes required include secure CI/CD and implementing DevOps best practices, securing orchestration and access controls, and securing the operating system and hardware.
- Disaggregated Deployments & ORAN: ORAN security is based on secured platform and communication between network functions. O-RAN alliance has identified several guiding principles for security including - authentication and authorization on all access, integration with external identity management system, role-based access, encryption of data, and implementation of logging.
- IOT & Edge Data Security: ensure that cached data is encrypted and protected. Boilerplate audits are done for edge sites.
- Open-Source Software: 5G architecture uses many open sources software, however before using them make sure to check publicly known vulnerabilities, perform security check using any standard tool and do a comprehensive security review.
- Automation: Networks beyond a certain size are impossible to maintain manually and therefore automation is important. Implement an intelligent and automated real time threat detection and mitigation automated solution.
- API Security: Ensure that APIs are built with strong security including identity management, access and authentication, anomaly detection and logging.
- Zero Trust Security:Finally implement Zero Trust security model that is based on principle that no user and network function can be trusted. Zero- trust shifts the focus away from network perimeter security, instead restricting access by internal and external users and software components through use of strong authentication and least privilege authorization.
Conclusion
5G represents a significant advancement in mobile communication. Its ability to support massive bandwidth and low latency enables several new and exciting use cases. However, the new architecture of 5G also exposes it additional security vulnerabilities. Securing 5G must be built in, not as an afterthought. Hence, a careful approach to these new aspects of cloud-native services, open-source software, APIs, automation, and edge is required.




















