Type in the name of any popular app into your favorite app store marketplace, and you’ll find not just the app you’re looking for, but almost certainly a whole bunch of knock-off apps that look and sound an awful lot like the one you were looking for. I’ll never forget the time I went to download Angry Birds, and found a zillion look-alike apps! It’s a rational approach for many developers: try to capitalize on a popular idea to get some downloads and development practice, monetize the app, and keep working on the next project.
That assumes, however, that the developers building the copycat apps are on the up and up. Monetizing a copycat app is one thing, but hiding ads and coding them to pop up out of context is another thing altogether.
That’s what HUMAN's Satori Threat Intelligence and Research Team found in December: a collection of apps - designed to look and sound like more popular and common apps - that were displaying numerous ads unexpectedly. The investigation, which the team named 'CopyCatz', found 164 apps with more than ten million downloads among them at the time of publication. What’s unique about this particular operation is the scale; there are a lot of devices that are committing fraud out in the world.
We can take a look at a single app to get a sense of how the whole operation worked:
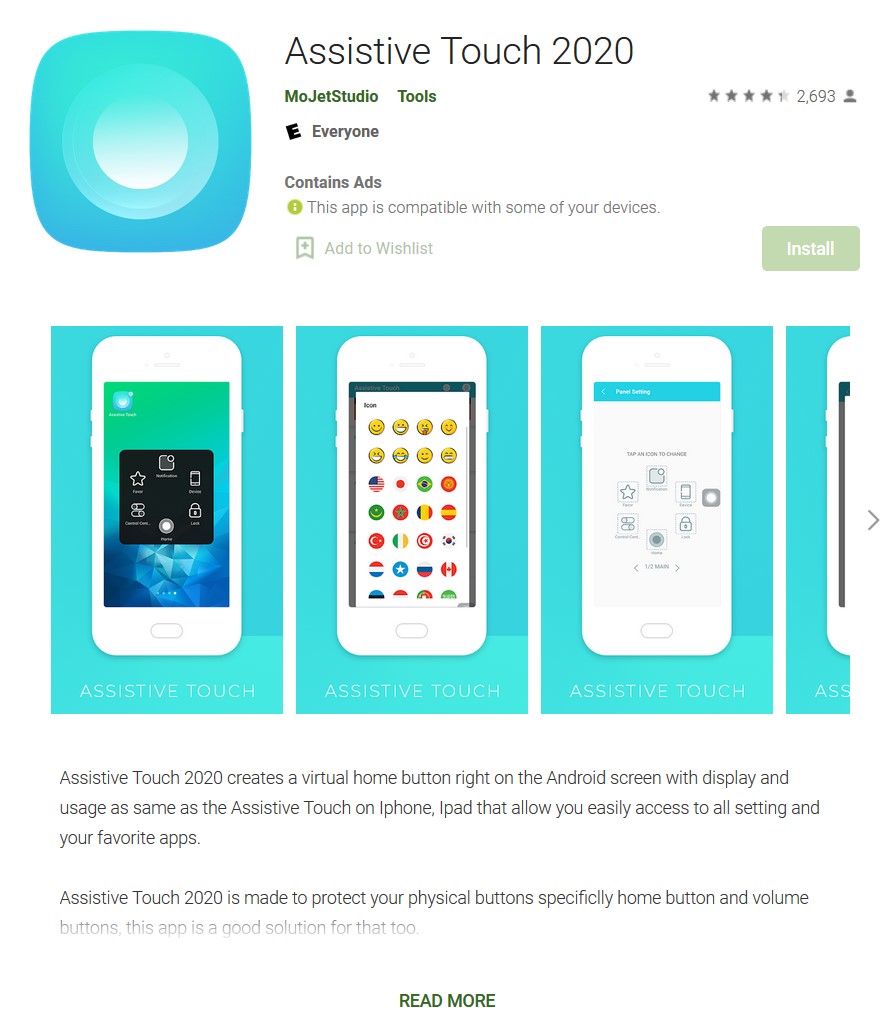
Assistive Touch 2020 was designed to mimic an app called Assistive Touch; the intention to deceive is transparent. The copycat app purports to be an all-purpose helper app, offering screen recording, memory cleanup, and accessibility tools.
But once it’s downloaded, it turns into a tool for a fraudster to show ads for as long as they can get away with it.
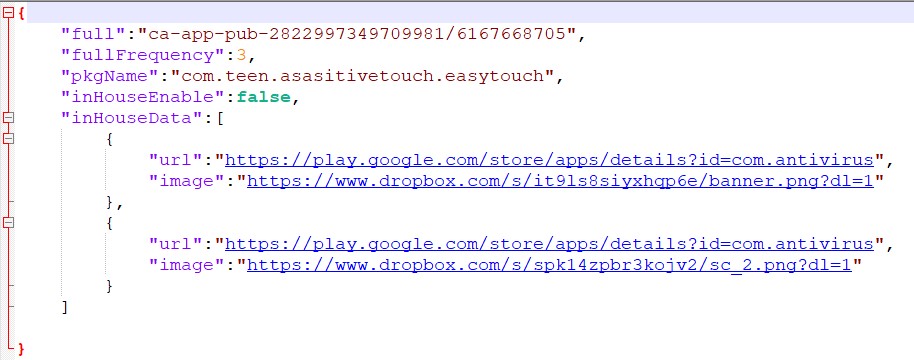
Above is a piece of code from the Assistive Touch 2020 app. What the code is doing is calling out to a command-and-control (C2) server hosted on Dropbox. (Note: Dropbox is one of the victims of this scheme and not a participant.) That C2 server responds back with instructions on how and when to pop ads up on the device. Many of those ads will appear when the app is closed or inactive, which falls under what’s known as “out of context advertising,” a type of ad fraud described by the IAB, one of the advertising world’s standardization bodies.
Here’s what one of those ads looks like when it pops up:

And that’s just one of the 164 apps that we found as part of this investigation. The Google Play Store has removed all of the apps, which will dramatically limit their ability to continue to spread. But the fraudsters behind the apps aren’t going to stop just because this operation was foiled. We’ve seen it before: fraudsters will have their apps pulled down only to retool and try again. It’s just a part of the cat-and-mouse game.
Our guidance is to always check that the app you’re downloading is the official version of the app you’re trying to download. Don’t fall for a copycat. And if your device starts to show ads unexpectedly, remove any suspicious apps from the device as soon as possible; don’t let the fraudsters use your device for nefarious ends.






















