New private wireless technology looks to bolster enterprise confidence amid growing wireless security concerns
As businesses become more reliant on wireless technology as a standard means of connectivity and communication for vital operations, security remains a growing concern.
Recent advances in private wireless networking that leverage cellular technology are bolstering the confidence of enterprises that demand the highest level of security for critical applications and uses cases that are now reliant on secure and reliable network connectivity.
Private wireless technology, or so-called 5G LAN, is a new type of wireless communication technology that operates across both licensed and unlicensed cellular spectrum typically within the less crowded 3.3 to 4.9 GHz mid-range bands. These networks use cellular technology as a local wireless network, hence the “5G LAN” moniker.
Until recently, the use of cellular technology required companies to leverage public 4G/LTE or emerging 5G services offered by mobile network operators (MNOs). But worries over the control and privacy of corporate data using a third-party public cellular service have largely limited the use of cellular technology within the enterprise.
Fears over public 5G privacy
Confidentiality and privacy routinely rate in the top security fears when it comes to the use of public 5G for enterprise connectivity. Worries over an increased attack surface, lack of visibility, and limited in-house knowledge are recurrent themes cited by enterprises.
In public 4G/5G networks, the collective concern is that with faster and more capable networks, MNOs will simply have more access to more data, including corporate data through 5G-connected devices. In the absence of strict privacy laws and governance, users of public 5G networks remain at the mercy of the MNO as to how their private data is used. Often, data and metadata are monetized by way of data correlation and trend analysis for marketing purposes.
New 5G LANs have been developed to solve the privacy and confidentiality issues intrinsic in public cellular connectivity through tight integration of cellular access points and mobile network services within the enterprise LAN footprint.
 Key Elements of Private Wireless Security (credit: Celona)
Key Elements of Private Wireless Security (credit: Celona)
Some advanced private cellular networks can be configured by enterprise IT network and security teams with any custom policy and traffic forwarding rules required at any time. This provides full control over enterprise data, management, and accessibility across the radio access network (RAN, a cellular version of a Wi-Fi network) and through the LAN. This means, the organization’s data is never made visible to anyone else.
All user and device data are secured and contained within the enterprise 5G LAN – encrypted from the device to the core of the network. Only metadata and system performance metrics are sent securely to cloud-hosted management systems – offering application delivery teams and wireless network engineers the visibility into critical application performance. Such customer metadata is never used for monetization and never sold to third parties.
Ensuring data confidentiality and integrity
5G technology offers secure 128-bit AES encryption over-the air. 5G LANs can further extend protection with 256-bit AES, offering quantum resistant cryptography that meets the NSA’s CNSA 2.0 requirements. Plus, 5G technology brings enhancements in key derivation and rotation where the master key is never shared or exposed, and the device’s identity is concealed for enhanced privacy.
In addition, data can be protected at each segment of the 5G LAN infrastructure. Advanced traffic management policies in some systems allow enterprises to not only segment traffic in a granular fashion but separately encrypt groups of devices or applications on a per-IP flow basis. These policies can be mapped directly to enterprise network segments, such as VLANs, VxLANs, firewall zones, or other enforcement points.
Identifying and authenticating devices
One key challenge for securing the volume of disparate endpoints on any enterprise network is proper identification and classification of the device -- two tasks which must be completed before security controls can be implemented. In fact, the first of five steps in the widely used Zero Trust Roadmap is to define the protect surface, which begins with a detailed asset inventory.
New 5G LANs combine the deterministic and immutable identities inherent in cellular technologies, such as the use of Subscriber Identity Modules or SIMs, with enterprise LAN security controls including device-specific policies, firewall rules. application service level requirements and VLAN segments.
Within private wireless networks, each endpoint has unique software and hardware identifiers, and follows a secure provisioning method the enterprise fully controls. This gives enterprises a dynamic asset inventory that is real-time and accurate.
Each SIM card embeds unique identifiers, such as the international mobile subscriber identity or IMSI used by 4G/LTE networks to authenticate users and protect their privacy.
Within the 5G world, these unique identifiers include the SUPI (Subscription Permanent Identifier) and SUCI (subscription concealed identifier). he SUPI effectively replaces the IMSI used in 4G network as the unique identifier for each subscriber in 5G. SUPI and SUCI are both identifiers used in mobile networks to authenticate users and protect their privacy.
The SUPI is a permanent identifier assigned to the user's SIM card, while the SUCI is a temporary identifier that is derived from the SUPI and is used to protect the user's privacy. The SUPI is used by the network to identify and authenticate the user when they connect to the network.
The SUCI is derived from the SUPI, and used to protect the user's privacy when they connect to the network. The SUCI is generated by the user's SIM card and is encrypted using a secret key that is only known to the SIM card and the user's home network. This makes it difficult for anyone to intercept or manipulate the SUCI and helps to protect the user's privacy and security.
This effectively eliminates inconclusive endpoint profiling and guessing what a device is, who owns it, or what applications it’s running. Endpoint devices are uniquely identified with immutable identities tied to the physical SIM and/or embedded SIM (eSIM). Within 5G LANs, this identity is used to derive a LAN-friendly unique identity for each connected device, allowing identification of the device across both the private cellular wireless and the enterprise LAN.
Mitigating long standing Wi-Fi security concerns
While conventional Wi-Fi has been the go-to wireless technology for many years, enterprise Wi-Fi networks are vulnerable to a wide range of attacks, including man-in-the-middle attacks, rogue access points, and packet sniffing.
These attacks can allow hackers to intercept data, steal sensitive information, and even gain access to the entire network. While Wi-Fi can be quite secure, Wi-Fi protocol vulnerabilities persist, legacy security suites continue to be used, and misconfigurations are extremely common.
In contrast, cellular networks are more difficult to attack, as their default configuration is equal to the security of a well-designed 802.1X secured network based on the latest WPA3-Enterprise suite.
New 5G LAN technology has brought new and exciting possibilities to enterprises that help eliminate many of these security vulnerabilities. Support for Zero Trust strategies with strong device identification, mutual authentication, granular end-to-end segmentation, and robust encryption -- plus integrations via APIs -- are just a few.
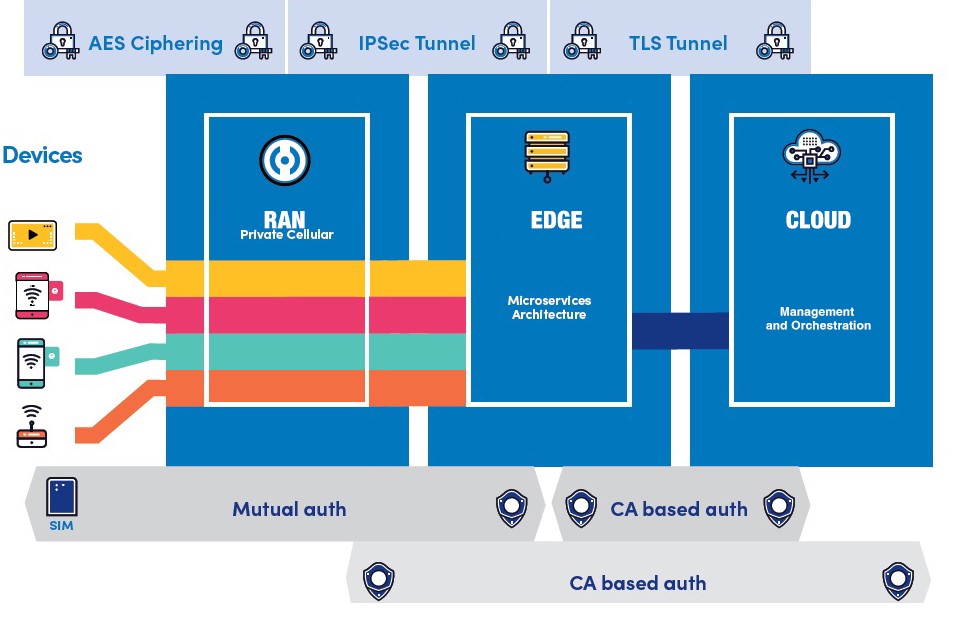 5G LAN Security Framework (credit: Celona)
5G LAN Security Framework (credit: Celona)
Client access using a cellular network is widely considered more secure due to the use of advanced media access methods, encryption technologies, strong authentication mechanisms, and the inherent security features of cellular networks. Mutual authentication is always enforced, ensuring the network and endpoint both authenticate to one another, further reducing opportunities for on-path attacks, spoofing, and rogue devices.
Unlike Wi-Fi where clients are constantly arbitrating or fighting for access to the wireless medium, user access and airtime is guaranteed, scheduled, and centrally coordinated by the network itself. This allows the organization to deliver on even the most demanding and latency-sensitive applications.
In addition, the 5G LAN infrastructure components will likely arrive already hardened and include TPM-based certificates required for building a trusted network. The device authentication protocols in 5G LANs often includes 5G-AKA and EAP-AKA’ which bring enhanced flexibility and security to the authentication process through translatable protocols appropriate for both cellular and Wi-Fi use and by adding signaling and data integrity.
While IoT has been excluded from many Zero Trust scopes due to the complexity of managing non-user-based devices and the diversity of the connectivity models, new 5G LAN technology now gives enterprises centralized visibility and control of corporate-managed cellular devices, non-traditional endpoints, and IoT devices, alongside traditional endpoints.
By tightly integrating with existing enterprise security policies, providing end-to-end traffic segmentation, mutual authentication between endpoints and 5G LAN infrastructure components, combined with strong device identification and encryption along the entire wired and wireless data path, organizations can now enjoy the strongest private wireless security posture available today.




















